A firewall is a crucial component of any computer’s security system, as it helps to protect against unwanted access and malicious attacks. Given the growing popularity of the Raspberry Pi, it is imperative to take security precautions to protect your device from unauthorized access and data breaches.
In this guide, we will walk you through the process of setting up a firewall on your Raspberry Pi, including the different types of firewalls available and the steps to configure them.
Why securing a Raspberry Pi with firewall is vital
Securing a Raspberry Pi with a firewall can provide several benefits, including:
Protection against unauthorized access: A firewall can be configured only to allow incoming connections from trusted sources, preventing unauthorized individuals from accessing the device.
Protection against malware: Firewalls can be configured to block incoming connections from known malicious IP addresses, helping to protect the device from malware and other security threats.
Control over network traffic: Firewalls can be configured only to allow specific types of network traffic, such as HTTP and HTTPS, while blocking others, such as P2P.
Monitoring of network activity: Firewalls can be configured to log all incoming and outgoing network traffic, providing a detailed record of all activity on the device. This can be useful for identifying security breaches and troubleshooting network issues.
Compliance with security regulations: In some cases, organizations may be required to comply with security regulations that mandate the use of firewalls.
Tip: Note that Firewall alone is not enough to secure your device; it should be used with other security practices such as keeping software up-to-date, using strong passwords, and being aware of the latest threats and vulnerabilities.
How to secure Raspberry Pi with Firewall
You can secure your Raspberry pi with a firewall using the following methods;
-
- Uncomplicated Firewall(UFW).
- IPtables.
Method One: Uncomplicated Firewall
UFW is a firewall management tool for Linux systems, and it can be easily installed and configured on a Raspberry Pi. Once installed, it allows for the management of incoming and outgoing traffic and the creation of firewall rules. For example, you can allow incoming traffic on port 22 for SSH while blocking all other incoming traffic.
Additionally, UFW allows for creating custom rules, such as blocking all incoming traffic from a specific IP address.
How to use an uncomplicated firewall to secure your Raspberry Pi
First, make sure that the Raspberry Pi is running the latest version of Raspbian(update) by executing the command
sudo apt-get update
Next, install UFW by running the command,
sudo apt-get install ufw
After installation, enable UFW by executing the command;
sudo ufw enable
Once UFW is enabled, it will block all incoming and outcoming traffic by default. But that can be changed. For instance,
You will be able to remotely access your Raspberry Pi by allowing incoming SSH( Secure Shell) connections if you execute the command below;
sudo ufw allow ssh
For allowing traffic on a specific port, use sudo ufw allow <port number>. For example,
sudo ufw allow 443
The above command will allow incoming traffic on port 443.
You can also allow incoming traffic from specific IP addresses using sudo ufw allow from <IP address> For example;
sudo ufw allow from 192.168.1.45
To check the status of UFW, execute the command;
sudo ufw status
If you want to disable UFW, you can run the command:
sudo ufw disable
UFW can add an extra layer of security to your Raspberry Pi. Still, it cannot take the place of other security precautions like using strong passwords, updating the operating system frequently, and staying away from unsecured networks. However, before making any changes, back up your Raspberry Pi’s configuration in case you need to go back.
Method Two: IPtables
IPtables is built-in software that is more of a command-line tool that can be used to secure a raspberry pi using a firewall. It is a bit more complex to use than UFW, but it offers more fine-grained control over the firewall. It can be used to create firewall rules for both incoming and outgoing traffic, and it also allows for creating custom rules.
Here are the steps to set up IPtables on a Raspberry Pi:
Install iptables
Open a terminal on your Raspberry Pi and run the following command to install IPtables.
sudo apt-get install iptables
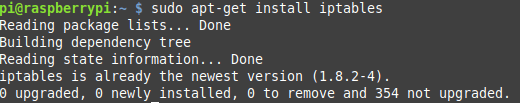
Install iptables
Back-up current IPtables rules
Before making any changes to IPtables, it’s a good idea to back up the current rules by running the command
sudo iptables-save > /etc/iptables.rules
Note that the above command may not execute. If that is the case, use the sudo su command to switch to the root user. See the image below;
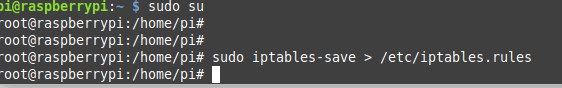
sudo su command
Set Default Policy
The default policy determines how IPtables will handle traffic that does not match the defined rules. To set the default policy to drop all incoming traffic and allow all outgoing traffic, run the following commands:
sudo iptables -P INPUT DROP
sudo iptables -P OUTPUT ACCEPT
Allow SSH traffic
To allow traffic on the SSH port (port 22) so you can remotely access your Raspberry Pi, run the following command:
sudo iptables -A INPUT -p tcp --dport 22 -jACCEPT
Allow HTTP and HTTPS traffic
To allow traffic on the HTTP (port 80) and HTTPS (port 443) ports, so you can access the web interface of your Raspberry Pi, run the following command:
sudo iptables -A INPUT -p tcp --dport 80 -j ACCEPT sudo iptables -A INPUT -p tcp --dport 443 -j ACCEPT
Save IPtables rules
To save the current IPtables rules, run the command
sudo iptables-save > /etc/iptables.rules
Load IPtables rules on boot
To load the IPtables rules on boot, you must create a new script in /etc/network/if-pre-up.d/ directory, with the following content:
#!/bin/sh /sbin/iptables-restore < /etc/iptables.rules
Make the script executable by running the command below.
sudo chmod +x /etc/network/if-pre-up.d/iptables
Conclusion
In conclusion, securing a Raspberry Pi with a firewall is essential in protecting it from malicious attacks and unauthorized access. Using IPtables as a firewall tool provides a powerful and flexible means of controlling incoming and outgoing network traffic. Following the step-by-step instructions outlined in this article, you can set up a basic firewall on your Raspberry Pi that will help keep it secure.
With the right tools and a little knowledge, you can keep your Raspberry Pi safe from the many threats on the internet today.